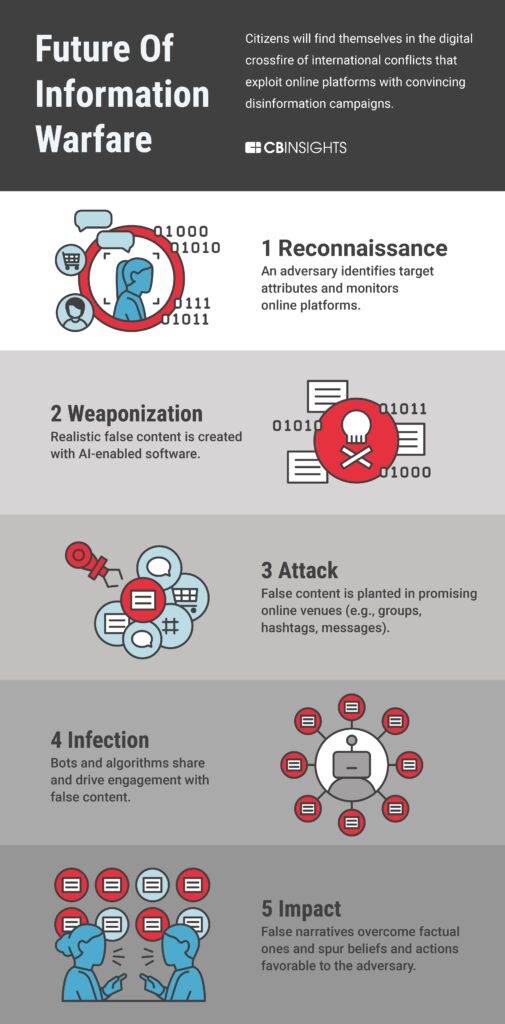
Cyber warfare has become a critical aspect of conflicts in today’s interconnected world, with attackers utilizing various tactics and techniques to disrupt or disable their opponents. Common types of cyber attacks include DDoS attacks, malware attacks, and phishing attacks, each aimed at causing significant damage to a target’s operations. Defensive tactics such as firewalls, encryption, and user training are crucial in protecting against cyber threats, while offensive techniques like zero-day exploits, social engineering, and backdoors are used by attackers to gain unauthorized access. Understanding the evolving landscape of cyber warfare is essential for organizations to effectively defend against this growing threat.
Cyber Warfare: Tactics and Techniques in the Digital Battlefield
Introduction
In today’s interconnected world, cyber warfare has become an increasingly important aspect of conflicts between nations and organizations. Cyber warfare involves the use of technology to disrupt or disable the operations of an opponent through the use of cyber attacks. In this article, we will explore some of the tactics and techniques used in the digital battlefield.
Types of Cyber Attacks
1. DDoS Attacks
One of the most common types of cyber attacks is the Distributed Denial of Service (DDoS) attack, where multiple systems flood a target’s server with traffic, making it unavailable to legitimate users. DDoS attacks can be used to disrupt the operations of a target or even take down critical infrastructure.
2. Malware Attacks
Malware attacks involve the use of malicious software to gain unauthorized access to a target’s systems or steal sensitive information. Malware can come in many forms, such as viruses, worms, and ransomware, and can be used to cause significant damage to a target’s operations.
3. Phishing Attacks
Phishing attacks involve the use of fraudulent emails, messages, or websites to trick individuals into revealing sensitive information, such as passwords or financial data. Phishing attacks are often used to gain access to a target’s systems or steal valuable information.
Defensive Tactics
1. Firewalls
Firewalls are a critical component of a strong cyber defense strategy, as they can help prevent unauthorized access to a network or system. Firewalls can be configured to block suspicious traffic and prevent malicious actors from gaining access to sensitive information.
2. Encryption
Encryption is another important defensive tactic in cyber warfare, as it can help protect sensitive data from being intercepted or stolen. By encrypting data, organizations can ensure that even if it is accessed by unauthorized users, it cannot be read or used.
3. User Training
One of the best defenses against cyber attacks is user training, as many attacks are successful due to human error. By educating users about the risks of cyber attacks and how to spot suspicious activity, organizations can help prevent many common attacks from succeeding.
Offensive Techniques
1. Zero-Day Exploits
Zero-day exploits are vulnerabilities in software that have not yet been discovered by the vendor, making them valuable tools for cyber attackers. By exploiting these vulnerabilities, attackers can gain access to a target’s systems without being detected.
2. Social Engineering
Social engineering is a technique used by cyber attackers to manipulate individuals into divulging sensitive information or performing actions that compromise security. By using psychological tactics, attackers can trick individuals into providing access to systems or information.
3. Backdoors
Backdoors are unauthorized access points into a system that allow attackers to gain entry without being detected. By creating backdoors in a target’s systems, attackers can maintain access even after their initial attack has been discovered and mitigated.
Conclusion
Cyber warfare is a constantly evolving field, with attackers developing new tactics and techniques to gain an advantage over their opponents. By understanding the types of attacks that can be used and implementing strong defensive strategies, organizations can protect themselves from the growing threat of cyber warfare.